If, without warning, senior management asks you to explain one or more pieces of your card program data, would you be prepared? No matter the topic, you do not want to be fumbling around for an answer. Memorizing key metrics is a good start, but understanding what is behind the numbers is more meaningful. This post describes four things your management may wonder or ask about, and what you should know to shine in the spotlight of their scrutiny.
Process Savings from Card Usage
Sharing your organization’s process savings via your Intranet and/or in a report to management showcases the value of your P-Card program, so be ready to explain:
- how you calculated the process savings
- how P-Cards save time and money for your organization compared to your other internal purchase-to-pay processes
- why your organization’s savings are higher or lower than industry averages (RPMG Research is a great resource)
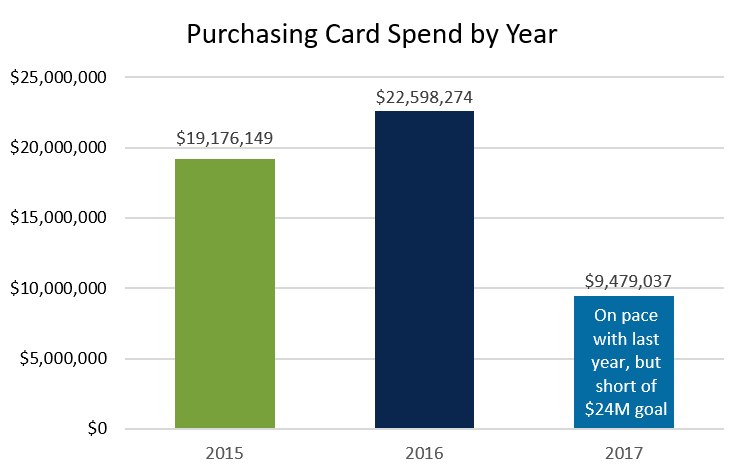
Card Spend
Relaying progress toward goals and how the current year compares to past years helps keep management informed; see examples below. Ensure you can explain any dips and/or upward spikes.
As a program manager, I once had to ask the organization president to sign off on the payment to our card issuer due to the unusual large dollar amount. While face to face in his office, he asked why the total was so high. Fortunately, I had researched that before approaching him, so I was able to answer.
Revenue Share
Announcing the revenue share (rebate) received from the issuer is always exciting, but do not stop with the dollar total. Include a note about where your organization stands, based on your current contract terms. Are you maximizing the revenue share opportunity? Why or why not?
Internal Fraud/Compliance
Apprising management of the compliance level with card policies and procedures is equally important.
- If you do not have issues, it is something to highlight, including the reasons for the success. Perhaps you maintain a current risk assessment that drives you to close any control gaps.
- If you have had internal fraud and/or compliance issues, be able to articulate the contributing factors and related remedies. Also, if there are more compliance problems today than in the past, determine why. Has compliance always been on the poor side, but new/better auditing is uncovering more now?
Internal fraud data, as well as process savings, are two things included within the P-Card Risk Analysis Template from Recharged Education. It is available for purchase or, by attending next week’s virtual workshop, you will receive a complimentary copy.
“Analysis without interpretation is just numbers.”
More Resources
Visit the P-Card Metrics webpage for related information.
About the Author
Blog post author Lynn Larson, CPCP, is the founder of Recharged Education. With more than 15 years of Commercial Card experience, her mission is to make industry education readily accessible to all. Learn more…
Subscribe to the Blog
Receive notice of new blog posts.